Collections Framework in Java –
1. What is the Collections Framework?
The Java Collections Framework (JCF) is a unified architecture for representing, storing, and manipulating groups of objects. It provides a set of interfaces, classes, and algorithms that make it easier to handle data structures like lists, sets, maps, and queues.
The framework is defined in the java.util package and supports operations such as searching, sorting, insertion, deletion, and iteration.
2. Key Features of the Collections Framework
- Unified architecture – All collections implement a common set of interfaces.
- Reduces programming effort – Reusable classes and interfaces.
- Increases performance – Through high-performance implementations.
- Supports interoperability – Easy to pass collections among APIs.
- Extensible – You can create your own collection classes.
3. Core Interfaces in the Collections Framework
| Interface | Description |
|---|---|
| Collection | The root interface for most collection classes. |
| List | An ordered collection (sequence) of elements. |
| Set | A collection that does not allow duplicate elements. |
| Queue | Designed for holding elements prior to processing. |
| Deque | Double-ended queue. Allows insertion/removal at both ends. |
| Map | A collection that maps keys to values (not part of Collection hierarchy). |
4. Common Classes and Their Use-Cases in the Java Collections Framework
The Java Collections Framework provides several ready-to-use classes to represent and manipulate groups of data. These classes implement core interfaces like List, Set, Queue, and Map, each designed for specific use-cases.
Let’s go through each group:
A. List Interface – Allows Duplicates and Ordered Access
The List interface represents an ordered collection (also known as a sequence). It allows:
- Duplicate elements
- Access to elements by index
- Insertion order is preserved
Common Implementing Classes:
| Class | Description |
|---|---|
| ArrayList | Backed by a dynamic array. Offers fast random access. |
| LinkedList | Doubly-linked list. Better for frequent insert/delete. |
| Vector | Thread-safe version of ArrayList. Slower due to sync. |
| Stack | Subclass of Vector. Implements LIFO (Last-In-First-Out) |
Example:
List names = new ArrayList<>();
names.add("Alice");
names.add("Bob");
System.out.println(names); // [Alice, Bob]
Use-Cases:
- Maintaining a sequence of items
- Ordered processing (like history, steps)
- Random-access reads (ArrayList)
- Queue-like behavior (LinkedList as a queue)
B. Set Interface – No Duplicates
A Set is a collection that does not allow duplicate elements. It is ideal when uniqueness is required.
Common Implementing Classes:
| Class | Description |
|---|---|
| HashSet | Backed by a hash table. No ordering of elements. |
| LinkedHashSet | Maintains insertion order of elements. |
| TreeSet | Sorted set. Maintains elements in natural or custom order. |
Example:
Set set = new HashSet<>();
set.add(10);
set.add(20);
set.add(10); // Duplicate, ignored
System.out.println(set); // Output may vary (unordered)
Use-Cases:
- Removing duplicates from a collection
- Fast membership checks (contains)
- Maintaining sorted or ordered unique elements
C. Queue Interface – FIFO Structure
A Queue is designed for holding elements before processing, following a First-In-First-Out (FIFO) approach.
Common Implementing Classes:
| Class | Description |
|---|---|
| PriorityQueue | Elements are ordered based on natural ordering or comparator. |
| ArrayDeque | A double-ended queue. Allows fast insertions/removals at both ends. |
Example:
Queue queue = new LinkedList<>();
queue.add("Task1");
queue.add("Task2");
System.out.println(queue.poll()); // Output: Task1
Use-Cases:
- Task scheduling
- Order processing
- Print queues, message queues
D. Map Interface – Key-Value Pairs
Although Map is not a subtype of Collection, it is an essential part of the Java Collections Framework. It is used to store key-value pairs, where each key is unique and maps to a specific value.
Common Implementing Classes:
| Class | Description |
|---|---|
| HashMap | Stores entries in no particular order. Fast for lookups. |
| LinkedHashMap | Maintains insertion order of key-value pairs. |
| TreeMap | Keys are kept sorted using natural or custom comparator. |
| Hashtable | Legacy thread-safe map. Slower than modern alternatives. |
Example:
Map map = new HashMap<>();
map.put("A", 1);
map.put("B", 2);
System.out.println(map.get("A")); // Output: 1
Use-Cases:
- Storing configuration (key-value) settings
- Caching data
- Counting frequencies (e.g., word counts)
- Mapping IDs to objects
Summary Table:
| Interface | Allows Duplicates | Maintains Order | Key-Value Support | Common Classes |
|---|---|---|---|---|
| List | Yes | Yes | No | ArrayList, LinkedList |
| Set | No | Depends on type | No | HashSet, TreeSet |
| Queue | Yes | Yes (FIFO) | No | PriorityQueue, Deque |
| Map | Keys: No | Depends on type | Yes | HashMap, TreeMap |
5. Utility Class – Collections
Java provides a Collections utility class with many static methods to operate on collections.
Common methods:
| Method | Description |
|---|---|
| Collections.sort() | Sorts a list |
| Collections.reverse() | Reverses elements in a list |
| Collections.max() | Returns the maximum element |
| Collections.min() | Returns the minimum element |
| Collections.shuffle() | Randomly permutes elements in a list |
Example:
List list = Arrays.asList(5, 1, 9);
Collections.sort(list);
System.out.println(list); // [1, 5, 9]
6. Differences Between List, Set, and Map
| Feature | List | Set | Map |
|---|---|---|---|
| Duplicates | Allowed | Not allowed | Keys not allowed to repeat |
| Ordering | Maintained | Depends on type | Based on key implementation |
| Access by index | Yes | No | Access by key |
| Key-value pairs | No | No | Yes |
7. Generics in Collections
What Are Generics?
Generics allow you to write type-safe, reusable, and flexible code in Java. When used with the Collections Framework, generics enforce compile-time type checking, ensuring that only the specified type of elements can be stored in a collection.
Generics were introduced in Java 5 to eliminate the need for typecasting and to catch type mismatch errors early — during compilation rather than at runtime.
Why Use Generics in Collections?
- Type Safety – Only the specified data type can be added to the collection.
- No Typecasting Required – Elements can be retrieved directly in the correct type.
- Improved Readability and Maintainability – Code is easier to understand.
- Early Error Detection – Catches bugs during compilation, not runtime.
With Generics – Type-Safe
List list = new ArrayList<>();
list.add("Hello");
// list.add(100); // Compile-time error
String str = list.get(0); // No casting needed
System.out.println(str); // Hello
Explanation:
- List means this list can only hold String objects.
- If you try to add an Integer (100), the compiler will flag an error.
- When retrieving elements, no casting is required.

Without Generics – Raw Type (Unsafe)
List list = new ArrayList(); // Raw type
list.add("Hello");
list.add(100); // Allowed at compile time
String str = (String) list.get(1); // Runtime error: ClassCastException
Explanation:
- Since the list is not type-restricted, it can store any object.
- You have to explicitly cast elements when retrieving them.
- If you cast the wrong type (e.g., casting Integer to String), it results in a runtime error.
Generic Syntax in Collections:
List list = new ArrayList<>();
Set set = new HashSet<>();
Map map = new HashMap<>();
Examples:
List numbers = new ArrayList<>();
Map scoreMap = new HashMap<>();
Set prices = new TreeSet<>();
Benefits Recap:
| Feature | With Generics | Without Generics |
|---|---|---|
| Type Safety | ✅ Yes | ❌ No |
| Compile-time Errors | ✅ Detected early | ❌ Detected at runtime |
| Need for Typecasting | ❌ No | ✅ Yes |
| Code Readability | ✅ High | ❌ Low |
8. Iterating Over Collections
What is Iterating?
Iterating (or traversing) is the process of accessing each element one by one from a collection like List, Set, or Queue to perform actions such as printing, modifying, filtering, or deleting.
Java provides two primary ways to iterate over collections:
- Using an Iterator
- Using an Enhanced for-loop (for-each loop)
A. Using Iterator
Iterator it = list.iterator();
while (it.hasNext()) {
System.out.println(it.next());
}
Explanation:
- list.iterator() returns an Iterator object.
- hasNext() checks if there are more elements.
- next() retrieves the next element in the sequence.
Why Use Iterator?
- Works with all collection types (List, Set, Queue)
- Supports safe element removal during iteration
- Useful when you need fine control over the iteration process
B. Using Enhanced For-loop (For-each Loop)
for (String name : list) {
System.out.println(name);
}
Explanation:
- Simplifies traversal when you only want to read elements.
- Java handles the iterator internally.
- Cleaner and more readable syntax.
Limitation:
- You cannot remove elements during iteration using this method.
- You don’t get index access.
When to Use Which
| Scenario | Preferred Method |
|---|---|
| Simple reading/traversal | Enhanced for-loop |
| Removing items during iteration | Iterator |
| Needing element index | Classic for-loop |
| Working with sets and queues | Either method |
Example with Both Methods:
List names = new ArrayList<>();
names.add("Alice");
names.add("Bob");
// Using Iterator
Iterator it = names.iterator();
while (it.hasNext()) {
System.out.println("Iterator: " + it.next());
}
// Using Enhanced For-loop
for (String name : names) {
System.out.println("For-each: " + name);
}
9. Thread-Safe Collections
| Legacy Thread-safe Collections | Modern Alternatives |
|---|---|
| Vector | Collections.synchronizedList() |
| Hashtable | ConcurrentHashMap |
| Stack | Deque |
10. Real-World Use Cases
- List: To maintain ordered collections like product lists, student names, etc.
- Set: For unique elements like user IDs, tags, roles.
- Map: For key-value associations like dictionaries, config settings, JSON data.
- Queue: For scheduling tasks, job queues, printer queues.
Here is a detailed explanation of How HashMap Works Internally in Java, including its architecture, operations (put, get), and enhancements in Java 8.
11. How HashMap Works Internally in Java (In-Depth)
HashMap is a part of the java.util package and implements the Map interface. It stores data in the form of key-value pairs, and is designed for fast access, providing average-case constant time complexity O(1) for insertion (put) and retrieval (get) operations.
However, worst-case complexity can degrade to O(n) in case of hash collisions, though Java 8 has optimized this using balanced trees.
Internal Data Structure
At the core, a HashMap uses an array of buckets, where each bucket is essentially a linked list (or tree) of Map.Entry objects.
Key Terms:
- Bucket: A location in the array indexed using a computed hash value.
- Entry Node: Each node holds a key, value, hash, and a reference to the next node.
- Array size: Power of two by default (e.g., 16, 32, etc.) to optimize indexing.
Working of put(K key, V value)
Let’s go through the process step-by-step.
1. Calculate hashCode() of the key
Every object in Java has a hashCode() method, which returns an integer hash.
int hash = key.hashCode();
2. Apply internal hash function
HashMap applies a supplemental hash function to spread the keys uniformly across the array.
hash = hash ^ (hash >>> 16); // better distribution
3. Determine the bucket index
The index in the array is determined using:
index = hash & (array.length - 1);
Using bitwise AND with (array.length - 1) ensures efficient computation when the array size is a power of two.
4. Check if bucket is empty
- If yes: Simply insert a new node at that index.
- If no: Collision has occurred.
5. Handle Collision
- Traverse the linked list or tree at that index.
- Use equals() to check if the key already exists.
- If yes → update the value.
- If no → append a new node at the end.
6. Convert to Tree (Java 8+)
If the number of entries in the same bucket exceeds 8, and the array size is at least 64, Java converts the linked list to a Red-Black Tree for better performance (O(log n) lookup).
Working of get(K key)
Retrieving a value from a HashMap involves:
1. Compute the hash and index:
Same as in the put method.
2. Access the bucket at computed index:
Node node = table[index];
3. Traverse the linked list or tree:
- Compare the key using equals() method.
- If found, return the corresponding value.
Java 8 Enhancements
Prior to Java 8, collisions were handled only by linked lists, which led to performance degradation in worst-case scenarios (e.g., many keys mapping to the same bucket).
Java 8 introduced:
- Red-Black Trees in buckets where collisions are frequent.
- Thresholds:
- Treeify threshold: 8 nodes in one bucket → convert to tree.
- Untreeify threshold: Less than 6 nodes → convert back to list.
- Minimum table capacity to treeify: 64
This significantly improves performance in large datasets with many hash collisions.
Internal Class: Node
In Java’s HashMap implementation, each entry is an object of Node (a subclass of Map.Entry).
static class Node implements Map.Entry {
final int hash;
final K key;
V value;
Node next;
// methods...
}
Load Factor and Resizing
- Load Factor: Determines when to resize the table.
- Default is 0.75.
- Threshold: When (capacity * load factor) is exceeded, HashMap resizes (doubles the size).
- On resizing, all existing entries are rehashed and placed in new buckets.
Advantages of HashMap
- Fast retrieval and insertion on average (O(1)).
- Efficient storage of large key-value data.
- Automatically resizes to maintain performance.
Drawbacks
- Not thread-safe (use ConcurrentHashMap in multithreaded environments).
- Performance can degrade if many hash collisions occur.
- null keys/values allowed (only one null key).
Example for Visualization
Map map = new HashMap<>();
map.put("id", "123");
map.put("name", "John");
map.put("city", "Delhi");
System.out.println(map.get("name")); // Output: John
Internally:
- "name".hashCode() is computed.
- Mapped to a bucket index.
- Stored as a node with key = "name" and value = "John".
- Retrieval uses the same hash/index logic and equals() for lookup.
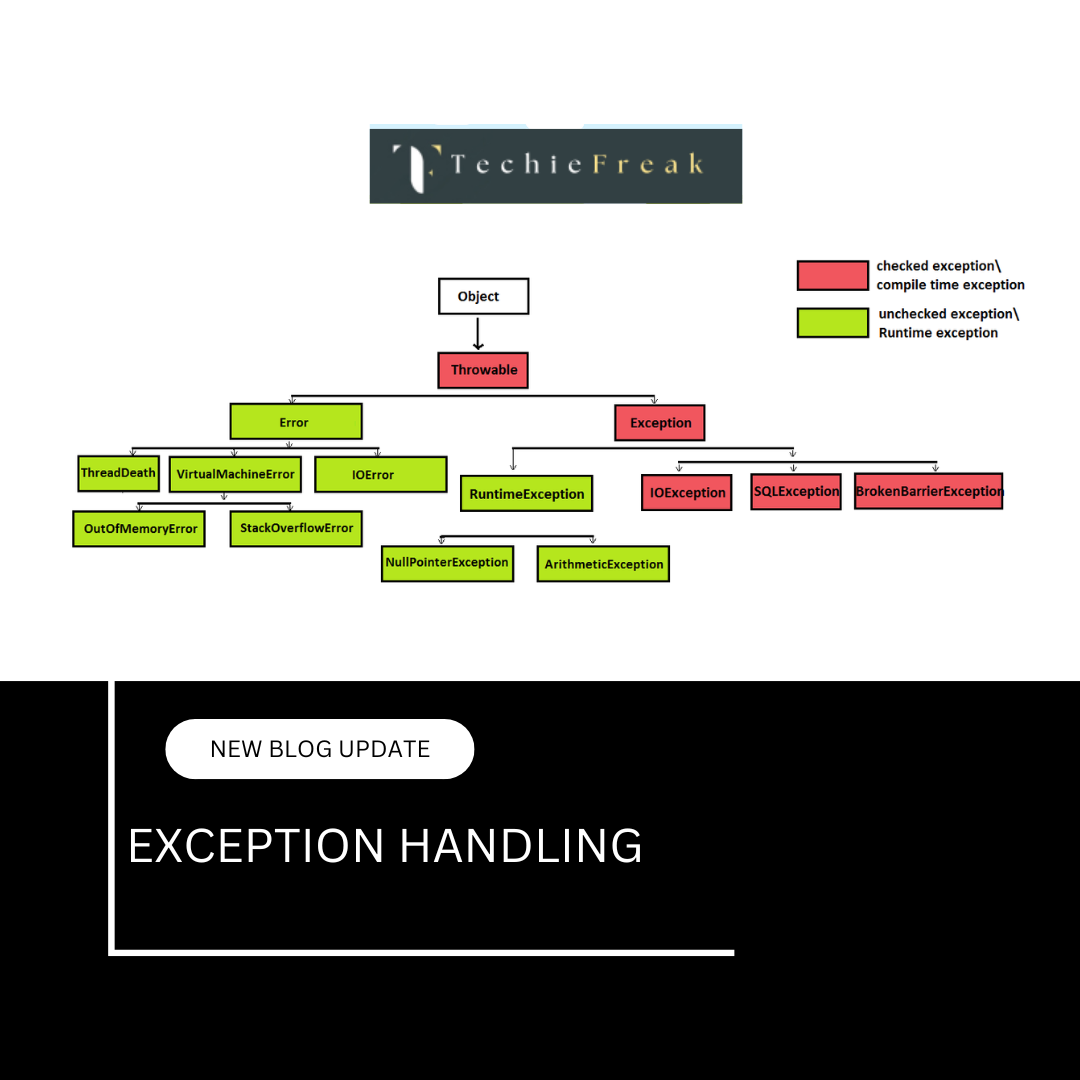
12. ConcurrentModificationException in Java
What is ConcurrentModificationException?
ConcurrentModificationException is a runtime exception that occurs when a collection is structurally modified while being iterated, using an iterator (like in a for-each loop or explicitly with Iterator), and the modification is not done through the iterator itself.
This is Java’s way of alerting you to unsafe modifications during iteration, which can lead to unpredictable behavior or data inconsistency.
Example Code
import java.util.*;
public class Demo {
public static void main(String[] args) {
List list = new ArrayList<>();
list.add("A");
list.add("B");
for (String item : list) {
list.remove(item); // Throws ConcurrentModificationException
}
}
}
Output:
Exception in thread "main" java.util.ConcurrentModificationException
Why Does It Happen?
Internally, collections like ArrayList and HashMap maintain a field called modCount that tracks the number of times the collection has been structurally modified (e.g., adding/removing elements).
- When an Iterator is created, it stores the expectedModCount, which is the current value of modCount.
- On every next() call during iteration, it checks if modCount != expectedModCount.
- If true, it means the collection was modified outside the iterator, and a ConcurrentModificationException is thrown.
This mechanism is part of Java's fail-fast behavior for many collections like ArrayList, HashSet, and HashMap.
What is a Structural Modification?
Structural modifications refer to:
- Adding elements
- Removing elements
- Clearing the collection
These change the size or internal structure of the collection.
Accessing or updating element values without altering the structure does not trigger this exception.
How to Avoid ConcurrentModificationException
1. Use Iterator.remove() instead of Collection.remove()
This is the correct way to remove elements while iterating.
List list = new ArrayList<>();
list.add("A");
list.add("B");
Iterator iterator = list.iterator();
while (iterator.hasNext()) {
String item = iterator.next();
if (item.equals("A")) {
iterator.remove(); // Safe way
}
}
2. Use a CopyOnWriteArrayList or Other Concurrent Collections
For concurrent/multithreaded environments, use fail-safe collections from the java.util.concurrent package.
List list = new CopyOnWriteArrayList<>();
list.add("A");
list.add("B");
for (String item : list) {
list.remove(item); // Safe in CopyOnWriteArrayList
}
These collections create a separate copy of the data on modification, allowing safe iteration even during modification.
Note: This comes with a performance tradeoff—slower writes, faster and safer reads.
When It Commonly Happens
- Modifying a collection inside a for-each loop.
- Removing entries from a Map while using keySet() or entrySet() in a loop.
- Updating a list from another thread during iteration.
Fail-Fast vs Fail-Safe Collections
| Type | Behavior on Concurrent Modification | Examples |
|---|---|---|
| Fail-Fast | Throws ConcurrentModificationException | ArrayList, HashMap |
| Fail-Safe | Iterates over a copy or snapshot | CopyOnWriteArrayList, ConcurrentHashMap |
13. Internal Working of ConcurrentHashMap
Overview
ConcurrentHashMap is a thread-safe, high-performance alternative to HashMap designed for concurrent access. It allows multiple threads to read and write simultaneously without compromising data integrity and without locking the entire map, making it ideal for multi-threaded environments.
- Available in java.util.concurrent package.
- Introduced in Java 5; significantly restructured in Java 8 for better performance.
Design Evolution: Java 7 vs Java 8
Java 7: Segmented Locking
- ConcurrentHashMap was implemented using a technique called Segmented Locking.
- The map was divided into multiple segments (default: 16).
- Each segment extended ReentrantLock and worked like an independent HashMap.
- Read operations were lock-free.
- Write operations only locked the segment, not the entire map.
Limitation: Fixed number of segments → limited scalability under heavy concurrency.
Java 8: Bucket-Level Locking with CAS
- Removed segments entirely.
- Introduced lock striping at node (bucket) level.
- Utilizes synchronized blocks on individual nodes for write operations.
- Uses CAS (Compare-And-Swap) operations via Unsafe API for atomic updates.
- Read operations are almost completely lock-free using volatile for visibility.
This redesign improved scalability, memory efficiency, and concurrency control.
Key Internal Concepts
1. Node Structure
Each key-value pair is stored as a Node in a bucket (similar to HashMap).
static class Node implements Map.Entry {
final int hash;
final K key;
volatile V value;
volatile Node next;
}
- volatile ensures visibility across threads.
- next forms a singly linked list (or tree, if bucket gets too crowded).
2. Table Structure
The main storage is an array of Node[], called table. The index is calculated using the hash of the key.
Node[] table;
Each index (bucket) can point to:
- A Node (for normal entries)
- A TreeBin (for balanced trees)
- A ForwardingNode (used during resizing)
3. Concurrency Control
Reads
- Done without locking.
- Values and links (next) are marked volatile, so visibility is guaranteed.
- If structure is stable, read proceeds quickly.
Writes
- Use CAS to acquire locks.
- If CAS fails (due to contention), fallback to synchronized on bucket node.
- Locks are very fine-grained, typically at the node level.
4. Compare-And-Swap (CAS)
- CAS is a low-level atomic instruction supported by hardware.
- In Java, CAS is accessed via the Unsafe class (or later via VarHandle).
- Used to update table cells or values without locks, offering better performance.
5. Treeification
- Like HashMap, if too many nodes are in one bucket (threshold = 8), it is converted into a Red-Black Tree using a TreeBin wrapper.
- Increases lookup speed from O(n) to O(log n).
6. Resizing
- When the table becomes too full, it doubles in size.
- Instead of blocking all threads, resizing is done incrementally by multiple threads cooperatively.
- A special ForwardingNode is used to indicate that a bucket has been moved to the new table.
When to Use ConcurrentHashMap
Use ConcurrentHashMap when:
- Your application involves multiple threads accessing or modifying a shared map.
- You need high read and write performance with minimal locking.
- HashMap causes data inconsistency or ConcurrentModificationException.
- Hashtable is too slow due to method-level synchronization.
Key Differences with HashMap
| Feature | HashMap | ConcurrentHashMap |
|---|---|---|
| Thread-safe | No | Yes |
| Null keys/values | One null key, many values | Not allowed |
| Performance | Fast (single-threaded) | Scales well with concurrency |
| Fail-fast Iterator | Yes | Weakly consistent iterator |
| Synchronization | None | Fine-grained (bucket/node level) |
Example Usage
import java.util.concurrent.ConcurrentHashMap;
public class Demo {
public static void main(String[] args) {
ConcurrentHashMap map = new ConcurrentHashMap<>();
map.put("id", "101");
map.put("name", "Alice");
System.out.println(map.get("name")); // Output: Alice
}
}
14. Internal Working of ConcurrentLinkedHashMap
Overview
ConcurrentLinkedHashMap is not part of the standard Java SDK. It is provided by third-party libraries like:
- Google Guava (now deprecated)
- Caffeine (modern replacement, highly optimized)
This data structure combines:
- The thread-safe, non-blocking behavior of ConcurrentHashMap
- The ordering capabilities (access-order or insertion-order) of LinkedHashMap
- The eviction capabilities (usually LRU) for caching use cases
Key Features Recap
- Maintains access order or insertion order
- Designed for high concurrency
- Non-blocking reads and writes using CAS (Compare-And-Swap) operations
- Implements Least Recently Used (LRU) or custom eviction strategies
- Provides weakly consistent iterators suitable for concurrent systems
Why Standard LinkedHashMap Isn't Enough
LinkedHashMap:
- Supports access order and insertion order
- Supports LRU eviction via removeEldestEntry() method
- Not thread-safe — must be externally synchronized
- Performance degrades under high concurrency
So in multi-threaded, caching scenarios, we need an alternative like ConcurrentLinkedHashMap.
Where It Comes From
- Guava’s MapMaker: Initially used to build ConcurrentLinkedHashMap (now deprecated)
- Caffeine: Modern, fast caching library that implements ConcurrentLinkedHashMap-style behavior with better performance and memory control
Internal Structure
The internals vary slightly between libraries (Guava vs Caffeine), but the underlying principles remain the same:
1. Core Data Structure
- Based on a segment-less ConcurrentHashMap structure.
- Uses a ConcurrentHashMap for key-value storage.
- Maintains a concurrent linked list or ring buffer to track access order or insertion order.
2. Ordering
- Every access or insertion updates a linked list node to track the usage.
- Nodes are moved to the tail when accessed (for LRU behavior).
- These nodes are linked using atomic references for non-blocking updates.
3. Eviction Policy (LRU or custom)
- A maximum capacity is set at initialization.
- Once exceeded, the eldest entries are evicted automatically.
- Eviction occurs asynchronously or during mutation operations to avoid blocking.
- Caffeine improves this by using a bounded buffer and asynchronous eviction threads.
4. CAS-Based Concurrency
- CAS (Compare-And-Swap) is used to atomically update pointers in the list.
- This avoids locks and enables lock-free updates, even when multiple threads are reading/writing simultaneously.
- CAS ensures thread safety with minimal contention.
5. Iterator Behavior
- Iterators are weakly consistent, meaning:
- They reflect some (but not necessarily all) modifications made to the map after the iterator was created.
- They do not throw ConcurrentModificationException.
- Ideal for non-blocking, real-time access.
Caffeine: A Modern Example
Caffeine is a high-performance caching library that implements all features of a ConcurrentLinkedHashMap and adds more (e.g., time-based eviction, size-based eviction, stats collection, refresh policies).
Example with Caffeine:
import com.github.benmanes.caffeine.cache.*;
Cache cache = Caffeine.newBuilder()
.maximumSize(100)
.expireAfterAccess(10, TimeUnit.MINUTES)
.build();
cache.put("user1", "John");
System.out.println(cache.getIfPresent("user1"));
Under the hood:
- Uses a custom concurrent hash structure
- Maintains ordering using ring buffers
- Evictions are handled by dedicated threads or tasks, not blocking main threads
Use Cases
- In-memory caching with eviction
- LRU-based session or object tracking
- Rate-limiting and access frequency tracking
- Application-level caching in high-performance systems (web servers, game servers, data pipelines)
15. HashMap vs ConcurrentHashMap
| Feature | HashMap | ConcurrentHashMap |
|---|---|---|
| Thread-safe | No | Yes |
| Null Keys/Values | 1 null key, many null values allowed | Null keys/values not allowed |
| Performance | Fast in single-threaded | Scales well with concurrency |
| Fail-fast | Yes (throws ConcurrentModificationException) | No (weakly consistent iterator) |
| Use Case | Single-threaded environments | Multi-threaded, concurrent systems |
When to Use:
- Use HashMap when thread safety is not needed.
- Use ConcurrentHashMap in high-performance concurrent scenarios.
16. Other Advanced Concepts (Optional Sections)
These topics are optional but recommended for completeness:
a. IdentityHashMap:
- Uses == instead of equals() for comparing keys.
- Used when object identity is required, not logical equality.
b. WeakHashMap:
- Keys are stored using weak references.
- Automatically removed from the map when key is no longer referenced elsewhere.
- Ideal for caching with memory sensitivity.
c. EnumMap:
- Optimized map for enum keys.
- Very efficient and memory-saving.
d. TreeMap vs HashMap:
- TreeMap is sorted, HashMap is unordered.
- TreeMap uses Red-Black Tree, HashMap uses hashing and chaining.
e. Fail-fast vs Fail-safe Iterators:
- Fail-fast: Throws exception on concurrent modification (e.g., ArrayList).
- Fail-safe: Iterates over a clone or snapshot (e.g., CopyOnWriteArrayList, ConcurrentHashMap).
f. Unmodifiable Collections:
List list = Collections.unmodifiableList(new ArrayList<>());
- Read-only collections.
- Modification operations throw UnsupportedOperationException.
Placement Summary in the Material
| New Topic | Where to Add |
|---|---|
| How HashMap Works Internally | After Section 10 |
| ConcurrentModificationException | After HashMap section |
| ConcurrentHashMap Working | After ConcurrentModificationException |
| ConcurrentLinkedHashMap | Right after ConcurrentHashMap |
| HashMap vs ConcurrentHashMap | As a separate comparative section |
| Advanced Collections (Optional) | As a final bonus section before conclusion |
Final Conclusion
The Java Collections Framework not only simplifies data handling in applications but also offers powerful structures for concurrent programming. Understanding the internal mechanisms of structures like HashMap, ConcurrentHashMap, and WeakHashMap is critical for writing efficient, robust, and scalable applications.
By mastering both the core concepts and advanced internals, Java developers can confidently choose and customize the right data structures based on performance, concurrency, and memory considerations.
.png)
.png)
